July 2015: WARNING: medium to serious threat exists in the form of the HTML/Tescrypt.D Ransomware virus.
A crypto locker virus is not a single virus, but rather a type of virus that uses similar attack strategies. These viruses do not destroy data, but rather render the data useless until such time as a ransom is paid.
For more on ransomware, please follow this link:
http://en.wikipedia.org/wiki/Ransomware
The companion screenshot shows a screenshot of Microsoft Security Essentials after portions of the Ransom:HTML/Tescrypt.D virus was detected and removed.
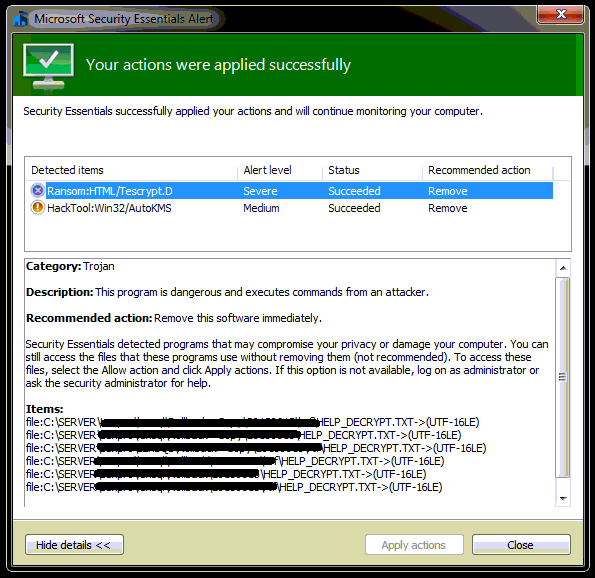
It can infect computers via malicious drive-by-download scripts from corrupted porn and shareware / freeware websites, or through spam email attachments, media downloads and social networks.
http://easyviruskilling.com/ways-to-remove-ransomhtmltescrypt-d-completely/:
http://easyviruskilling.com/ways-to-remove-ransomhtmltescrypt-d-completely/
The true threat of the HTML/Tescrypt.D lies not in the unwanted popups, but in the backdoor it creates to the local PC. This allows any number of malicious applications to be installed. On a business computer this may result in key-loggings software, capturing every keystroke. Leaving online banking activities vulnerable.
Eventually, once the HTML/Tescrypt.D code has spread through the system, it will eventually force the computer to a standstill and demand payment to release the files: ransomware.
Security measures include:
- user awareness
- established, up to date anti-virus software
- regular backups
As a simple precaution, do a search on your computer, and search for “HELP_DECRYPT.TXT“. In the event that you do in fact find such files on your computer, please contact IT support immediately. Your computer may be infected with a Ransomware virus.
The message is clear – data security starts with controlled access to the computer and restricting unwanted applications. In fact, where unwanted applications appear, this may be an indication that malicious code is already at work.
In the event of unchecked ransomware infestation, the choice is to pay the ransom, or restore a backup.
