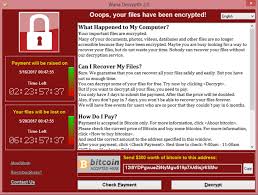
WannaCry Ransomware: Which systems are vulnerable and how can infections be prevented?
The recent WannaCry Ransomware outbreak is one of the most virulent and widespread attacks of this kind. As of 17 May 2017, only 5 days after its release, the total estimated impact was as follows:
- 200,000+ infections in 150+ countries
- Major hospitals in the UK were forced to divert patients to other facilities as their systems were taken down by the malware.
- Departure screens in train stations in Germany were showing the malware screen.
- Point of Sale software in China was impacted, forcing the use of cash to pay for services.
- The attackers received approximately $70 000 as ransom payments.
The timeline of the attack was as follows:
- 14 March 2017 – Microsoft releases MS17-010
- 14 April 2017 – The Shadow Brokers group releases the exploit.
- 12 May 2017 – WannaCry is released and starts spreading globally
- 13 May 2017 – Microsoft releases further releases for unsupported versions of Windows.
- 14 May 2017 – A kill switch is discovered for the first release of WannaCry
- 15 May 2017 – A second version of WannaCry is released, which is shortly afterwards also disabled by utilizing a kill switch.
- 17 May 2017 – WannaCry 2.0 is released. This version does not have a kill switch.
From the above timeline it can be seen that from the release of the exploit, to the release of the ransomware took only 28 days. From there the attackers have updated the malware twice again in only 5 days. This speed of deployment is unprecedented. However it must also be noted that Microsoft released the first patch a full 30 days before the exploit became available. If this patch was installed in the 58 days following its release, the systems where it was installed would have been immune to the malware. It is currently estimated that as much as 50% of business systems in the world are still not patched and therefore vulnerable to infections.
Furthermore, Microsoft released a further patch for End of Life (EOL) systems. This is not normal practice but is was done in this case to prevent the spread of the malware throughout the whole network. Currently it is estimated that up to 5% of business systems in the world are using unsupported versions of Windows. These systems are especially vulnerable to these kinds of attacks and it is strongly recommended that they are upgraded to a supported version as soon as possible.
The most common unsupported Windows version currently in use is Windows XP.
Remediation
The following versions of the Windows operating system are currently still supported by Microsoft and applying patch MS17-010 will resolve this issue. Note that this patch was released in March 2017, so systems that are regularly updated should already have the patch installed.
Supported versions of Windows:
- Windows Vista, Windows 7, Windows 8.1, Windows 10
- Windows Server 2008, Windows Server 2008 R2, Windows Server 2012, Windows Server 2016
The following versions of the Windows operating system have reached EOL (End of Life) and are no longer supported. However Microsoft did release KB4012598 on 13 May 2017 and installing this patch will stop the spread of the current versions of WannaCry. It is strongly advised that these systems are upgraded to a supported version of Windows, as they may still be vulnerable to future variants of this and other malware.
EOL versions of Windows that can install KB4012598:
- Windows XP SP3, Windows 8,
- Windows Server 2003 SP2
For systems that cannot be patched, Microsoft has provided a workaround. However this is only a temporary fix and these systems should be patched as a matter of extreme urgency:
Disable SMB v1:
- Windows Vista, Windows 7, Windows 8, Windows 8.1, Windows 10
- Windows Server 2008, Windows Server 2008 R2, Windows Server 2012, Windows Server 2016.
No workaround exists:
- Windows XP SP3
- Windows Server 2003 SP2
- Windows 2000
- Windows Millennium
- Windows 98
- Windows 95
More information on the workaround can be found at:
https://support.microsoft.com/en-us/help/2696547/
Q&A
- What is the relationship between EternalBlue and WannaCry?
EternalBlue is the exploit released by The Shadow Brokers. This is spread through the internet and establishes a back door into the infected systems. WannaCry is the ransomware that uses this exploit to disrupt the use of the computer systems and then demands a ransom from affected businesses and users.
- How does the EternalBlue/WannaCry exploit spread?
The first infection is normally delivered via email or the web, where the user inadvertently clicks on an infected link or downloads a file from the internet. Once the first workstation is infected the EternalBlue exploit then spreads using the SMB protocol. This protocol is used to share files and directories between workstations and servers on the same LAN and for workstations to request services from servers, such as Saving or Opening Files. SMB is an integral part of the Windows operating system and can therefore not be disabled. The current versions of EternalBlue only exploit SMBv1. However SMBv2 may also be impacted in future.
Recommendation
It is advised that versions SMBv1 and SMBv2 are disabled and only SMBv3 used.
SMBv3 was released as part of Windows 8 and Windows Server 2012 and are available in all subsequent releases.
Windows 8.1 and Windows 10 use SMBv3.
MrBackup
